Blue Teaming
4 SOC tools beginner blue teamers should learn
How to get good at these fundamental SOC tools and their related skills.
Table of Contents
Security Operations Center (SOC) analysts rely on a variety of tools that help them keep an eye on their domains.
However, simply relying on tools to get the job done, and failing to understand the fundamental processes and methodologies behind them, could be a costly mistake for an analyst to make.
We found that nearly a third (29.5%) of professionals rated Incident Handling Processes and Methodologies to be the most important knowledge domain for SOC analysts to master:
My key takeaway from the most challenging incidents I’ve worked on is the criticality of having efficient IR (incident response) processes and ensuring the real basics are done right.
So it makes sense for any security leadership team (and up-and-coming analyst) to prioritize these essential skills, as the vast majority of incidents I’ve handled across eight years in the field weren’t triggered by APTs chaining multiple zero-day exploits to compromise an environment—human error, misconfigurations, and poor incident response processes played a key role.
Sebastian Hague, Defensive Content Lead at Hack The Box.
SOC teams need to learn the language of their tools and understand how they are configured to avoid oversights.
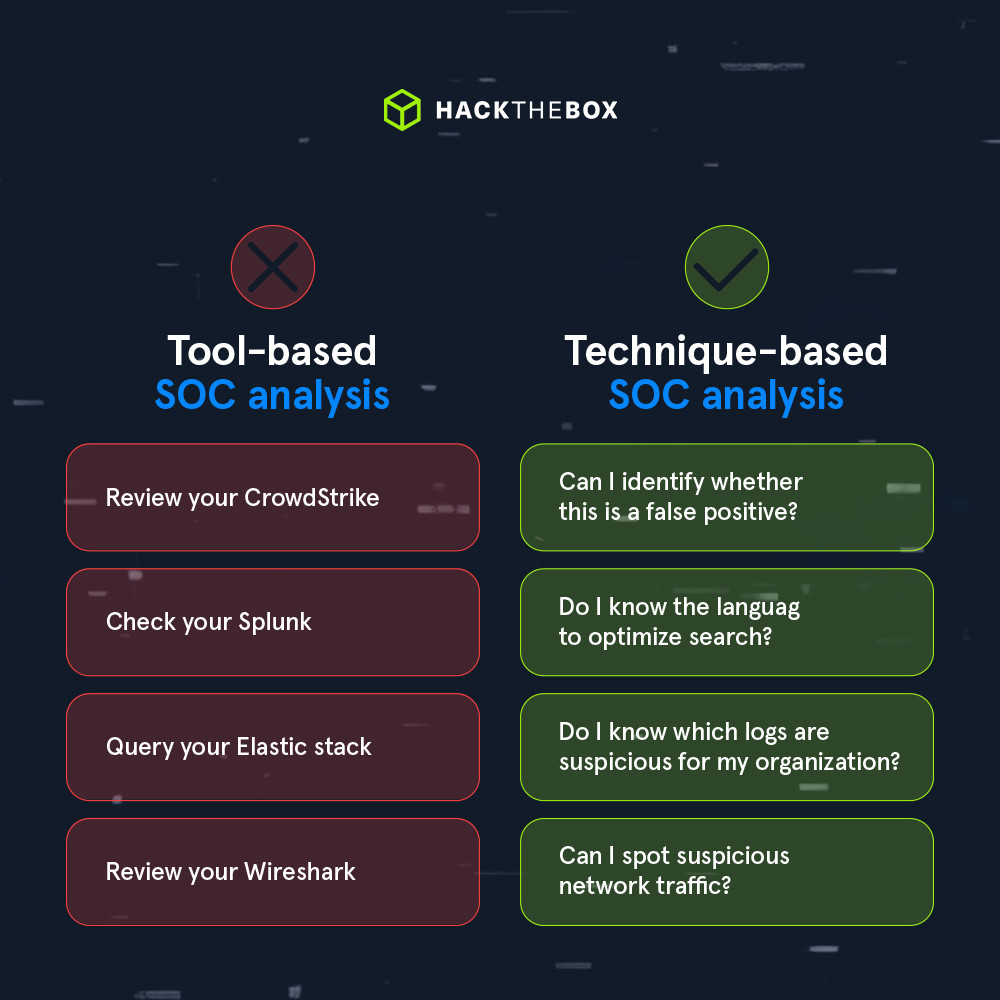
Respect the methodology behind blue team tools
While SOC tools can help automate and lighten the workload for many analysts, the techniques over tools mindset applies to all cybersecurity professionals.
Monitoring tools won’t be able to spot every case of suspicious activity, so a SOC analyst also needs critical thinking skills.
Learning your environment is an essential first step, as the key to spotting anomalies is understanding what’s considered “normal” in our environment.
For example, with Windows event logs, regular changes to system audit policies may be normal in your organization but could be considered a threat in another.
SOC tools are a must in modern enterprise environments, but relying solely on these is a big mistake many big organizations make to this day.
At the end of the day, it is the human who develops, fine-tunes, and manages those tools. For example, an attacker installs a remote management tool (also called rmm tools) like anydesk, teamviewer screenconnect, etc.
These mentioned tools are legitimate and are used for remote support capabilities. Well, the bad news is that attackers love using enterprise tooling to attack the environment.
An EDR or SIEM or Antivirus will not catch installation and usage of this tool as they are simply not malicious. But in reality, in our example, a malicious entity installed it for persistence and remote access.
What makes this action malicious is the context and baselining of the environment.
While the EDR did not catch this, a SOC analyst seeing this tool being used in a workstation will further look into this and confirm whether this tool is part of normal operations or not.
It is the context and knowing your environment that makes this malicious or suspicious.
After an analyst has spotted this and followed the standard incident procedure they can fine-tune their SOC tooling (SIEM / EDR) to catch such activity should it happen in the future.
Abdullah Yasin, Senior Defensive Content Engineer, Hack The Box.
Types of SOC analyst tools
Before diving into the best tools for cybersecurity analysts, we’ll cover the main types and their use cases for defensive security and incident response (DFIR).
-
Endpoint Detection and Response (EDR): Detect and respond to suspicious activities on endpoints like laptops, mobile devices, and servers.
-
Security Information and Event Management (SIEM): Collect and analyze data from an organization's applications, devices, servers, and users in real-time.
-
Vulnerability management (VM): Scan networks and computer systems for signs of vulnerabilities.
-
Intrusion detection systems (IDS): Observe network traffic, alerting security teams of any potential security threats.
-
Access management tools: Help organizations manage access rights and user permissions.
SIEM vs EDR
If I want to go for one I will choose SIEM. The reason it is SIEM is because ideally in SIEM we will have all of our logs (process logs, security logs, firewall logs, authentication logs, web logs, ids logs, EDR logs as well if we have one).
This provides much better coverage on our network than any other of those tools. We can set up detections using logic between all of the discussed sources, perform threat hunting utilizing old data (but it depends on the retention period of the organization).
SIEM is the backbone of a modern SOC and it is a MUST.
One thing EDR stands out for is its enriched process analysis and correlation mechanism, which can also be done in SIEM, but is much harder to implement.
Master Windows event log analysis with HTB Academy

-
Gain practical skills for investigating Windows event logs to uncover potential security breaches.
-
Learn the process of installing or updating Sysmon and present real-world examples of detection, including identifying DLL hijacking, unmanaged PowerShell/C-Sharp injection, and credential dumping.
-
Delve into Event Tracing for Windows (ETW) and its architecture, learn its components, and how to interact with it.
The best tools for SOC analysts
There are a variety of SOC tools on the market, likely more than we can cover in a single blog post! Here, we will talk about a handful of the most common ones.
1. CrowdStrike Falcon
The CrowdStrike Falcon AI-native platform consolidates EDR, identity threat detection and response (ITDR), SIEM, data protection, IT automation, and managed threat hunting in a single solution.
The fully cloud-based solution is popular amongst remote security teams. When paired with its broad set of features, CrowdStrike Falcon is a commonly used SOC tool. Some elements to highlight include:
-
MITRE ATT&CK mapping: Maps detected threats to the ATT&CK framework, providing security teams valuable context about the attacker’s goals and methods, helping to spot vulnerabilities.
-
Threat simulation: Visualizes “what if” scenarios without disrupting end users.
-
Extended Detection and Response (XDR): Goes beyond just endpoint detection and monitors other sources including firewalls, cloud workloads, and user activity.
Who is CrowdStrike Falcon for?
✅Organizations with multiple devices and platforms: CrowdStrike’s unified platform makes it easier to monitor complex IT environments.
✅Businesses concerned with advanced external threats: AI and machine learning (ML) are well-suited for detecting sophisticated threats outside an organization.
✅Companies looking to automate: Falcon’s automated features can save significant monitoring time.
Who isn’t CrowdStrike Falcon for?
❌Insider threats: CrowdStrike focuses on detecting unauthorized users, with internal bad actors potentially being overlooked.
❌Limited budgets: This solution is on the costly side, meaning smaller businesses might want to start with a cheaper option.
❌Limited security expertise: Falcon is user-friendly but contains many advanced features that would be wasted if an organization doesn’t have a dedicated security team.
|
Key features |
Pros |
Cons |
Deployment |
|
|
|
On-premise, cloud, multi-cloud, and hybrid deployments. |
2. Splunk
Splunk is a highly scalable, versatile, and robust data analytics software solution known for its ability to ingest, index, analyze, and visualize massive amounts of machine data.
Splunk can drive various initiatives, encompassing cybersecurity, compliance, data pipelines, IT monitoring, observability, and overall IT and business management.
When it comes to cybersecurity, Splunk can play a crucial role as a log management solution, but its true value lies in its analytics-driven Security Information and Event Management (SIEM) capabilities.
Splunk as a SIEM solution can aid in real-time and historical data analysis, cybersecurity monitoring, incident response, and threat hunting. Moreover, leveraging user behavior analytics empowers organizations to enhance their detection capabilities.
Who is Splunk for?
✅Experienced teams: SOC teams looking for an SIEM solution to boost their performance, who understand the fundamentals.
✅People with time: To properly manipulate the data, users need to learn and understand Splunk Processing Language (SPL).
Who isn’t Splunk for?
❌IT teams with little security knowledge: Individuals without a specific cybersecurity background may not get all of the benefits Splunk offers.
❌Plug in and go users: You need to take the time to learn the language and understand how to get the right answers, meaning a time investment is non-negotiable.
|
Key features |
Pros |
Cons |
Deployment |
|
|
|
On-premises, cloud, hybrid and fully managed Splunk cloud deployment. |
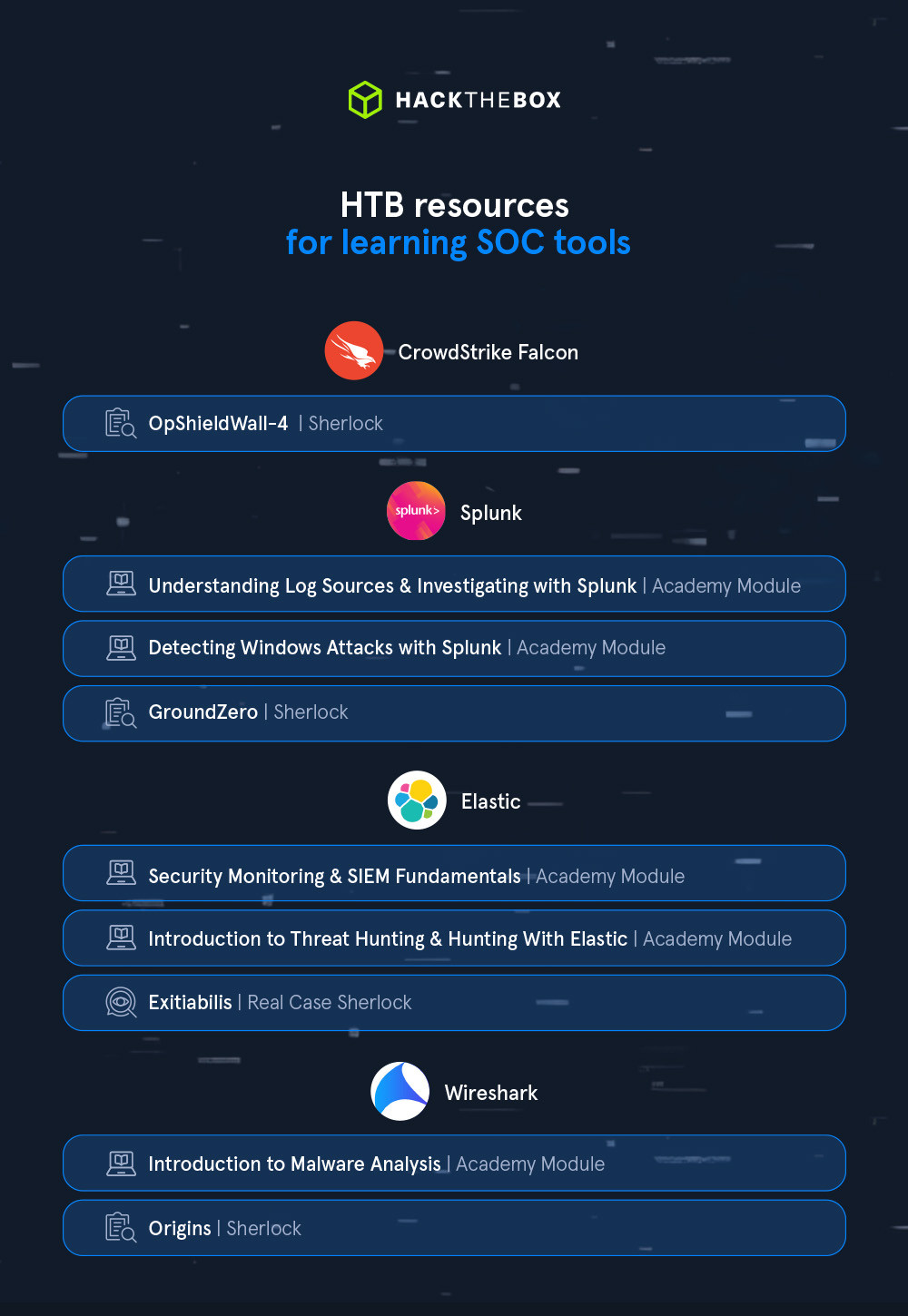
💡Resources to learn Splunk:
3. Elastic Stack
The Elastic stack, created by Elastic, is an open-source collection of mainly three applications, Elasticsearch, Logstash, and Kibana, (they are sometimes referred to collectively as ELK) that work together to offer users comprehensive search and visualization capabilities for real-time analysis and exploration of log file sources.
The three main components of the Elastic stack are:
-
Elasticsearch: A JSON-based search engine, as the core component of the Elastic stack, it handles indexing, storing, and querying.
-
Logstash: Responsible for collecting, transforming, and transporting log file records.
-
Kibana: The visualization tool for Elasticsearch documents. Users can view the data stored in Elasticsearch and execute queries through Kibana.
The Elastic stack can be used as a Security Information and Event Management (SIEM) solution to collect, store, analyze, and visualize security-related data from various sources.
As SOC analysts, we are likely to extensively use Kibana as our primary interface to work with the Elastic stack, which means learning Kibana Query Language (KQL), the user-friendly query language designed specifically for searching and analyzing data in Kibana.
This can simplify the process of extracting insights from your indexed Elasticsearch data, offering a more intuitive approach than Elasticsearch's Query DSL.
Who is Elastic for?
✅Large amounts of data: For companies with large amounts of datasets, the Elastic stack can run their data operations.
✅Experienced SOC teams: Kibana requires SOCs to learn the KQL to get the most of Elastics insights.
Who isn’t Elastic for?
❌ Time-poor teams: To manage and get optimum results from the Elastic stack, teams need to invest time into setting it up and learning the language.
❌Companies that are scaling: Many users report issues when data volume increases. Meaning growing companies might opt for a simpler solution.
|
Key features |
Pros |
Cons |
Deployment |
|
|
|
On-premise, cloud, and hybrid deployments. |
💡Resources to learn Elastic:
4. Wireshark
Wireshark is a network traffic analysis tool that captures packets, copying them rather than intercepting, which means that network monitoring tools won’t be able to spot that Wireshark is running. These captured packets contain information, such as the source and destination of IP addresses, different protocols, and port numbers, in addition to the actual data being sent over the network.
Wireshark is a simple but popular tool due to the user-friendly graphical user interface (GUI), which sorts and color-codes packets, making it easy for analysts to spot malicious behavior.
Who is Wireshark for?
✅Beginner analysts: Wireshark can be a great tool for beginners looking to understand network traffic and the different packets.
✅Troubleshooters: This tool can be used to see why a network is behaving a certain way, rather than detection.
Who isn’t Wireshark for?
❌Multiple networks: Wireshark can only sniff packets between your local computer and the remote system it is talking to, not all systems on the network.
❌Detection: Wireshark isn’t an IDS, it won’t tell you if something’s wrong, but it may display some packets in different colors.
|
Key features |
Pros |
Cons |
Deployment |
|
|
|
On-premise. |
💡Resources to learn Wireshark:
Knowledge is power
Knowledge of fundamentals should always take priority over a deep knowledge of the tools.
Without a basic knowledge of Windows, you may struggle to effectively analyze Windows event logs, for example.
Do you lack a deep understanding of network traffic packets? Then you could be wasting time by deploying Wireshark without taking the time to learn about them.
If you take only one lesson away from this post, let it be this:
Take the time to learn the fundamentals, the languages, and the use cases for each tool in your SOC toolbox.
The solution isn’t always to throw tools at problems!
You can learn the fundamentals and essential knowledge for SOC analysts with our top-tier defensive security certification, CDSA (Certified Defensive Security Analyst).