Blue Teaming
Decoding Windows event logs: A definitive guide for incident responders
Windows event logs can provide valuable insights when piecing together an incident or suspicious activity, making them crucial for analysts to understand.

sebh24,
Apr 23
2024
Table of Contents
This post is based on the Hack The Box (HTB) Academy module on Windows Event Logs & Finding Evil. The module equips learners with the skills to investigate event logs for detecting and analyzing malicious behavior.
You can learn more by browsing the catalog of free or advanced cybersecurity courses on the HTB Academy!
What are Windows event logs?
Windows event logs are a record of events that have occurred on a computer running the Windows OS.
They include information about the system, applications running on it, providers, services, and more.
Windows event logging offers comprehensive logging capabilities for application errors, security events, and diagnostic information. Cybersecurity analysts & SOC teams use “event log analysis” to detect suspicious activity and signs of intrusion.
Logs are categorized as "Application", "System", and "Security", to organize different events:
-
Application event logs: Any event that has occurred gets logged by an application.
-
System event logs: Any event that relates to the system or its components.
-
Security event logs: Security-related events, such as login attempts or file deletion, are logged in this type of log.
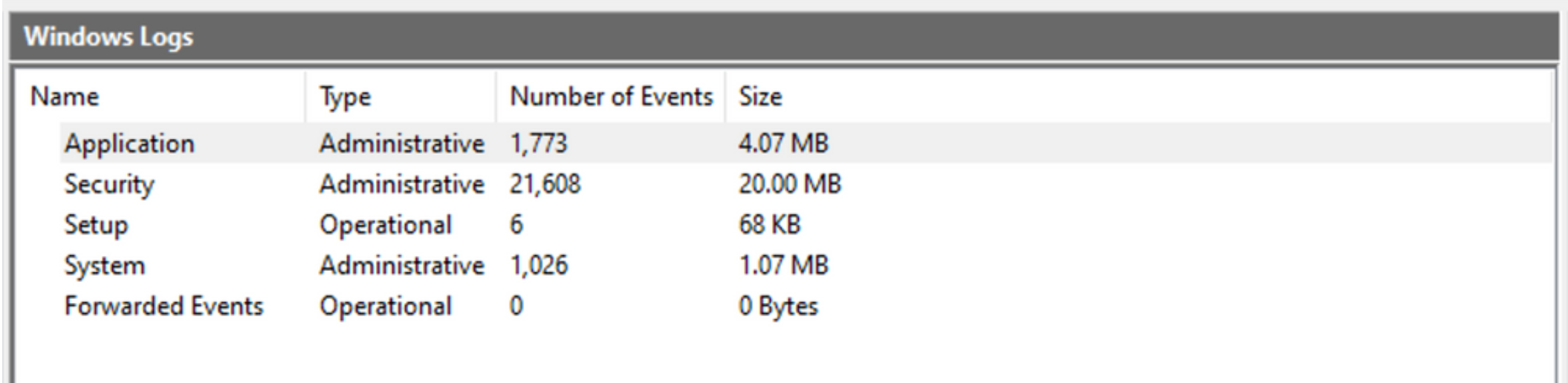
Accessing the Windows Event Viewer as an administrative user allows us to explore the various logs available.
Why is event log analysis important?
Imagine this scenario: an application on your Windows machine fails, with a mysterious message that doesn’t tell you much about the problem.
Is it a security issue, or a random system error?
This is where Windows event logs can reveal the truth.
Event log analysis is incredibly important for all organizations and brings many benefits:
-
Regulatory compliance: storing event logs helps organizations adhere to specific regulations that dictate how data is archived and analyzed.
-
Troubleshooting: when logs are regularly reviewed, errors are spotted and amended much faster. Some errors can be caught before they occur, saving time and money in remediation.
-
Improved security posture: Keeping on top of event logs makes it easier to spot anomalies, contain threats, and prioritize responses.
-
Better customer experience: if an organization offers customer-facing tools and applications, regular event log analysis will help to prevent disruptions.
Abdullah Yasin (CyberJunkie), Defensive Content Engineer, Hack The Box, shared his insights on the importance of effective event log analysis:
Understanding different event log sources and eventID is one of the most crucial pieces of knowledge an analyst should have. As a defender, you must be able to trace back to the source of malicious activity starting from just one event.
If you could paint a story of how a certain event occurred, and what events led to this, you can answer the who, when, and why in context to the incident.
Context is key in event log analysis. As every event tells a story. We just need to find it, contextualize it, and validate it to reach our goal.
I will give a technical example:
Let's say you are a SOC analyst and received an alert about possible credential dumping using mimikatz on one of the endpoints.
To understand the true extent of this event, we need to understand what events occurred that led to this malicious event.
By doing this, you’ll transform a single event into an incident and potentially uncover other activities by an adversary.
Expanding on our example, you may need to trace back the origins of the user account used to dump credentials:
How did that user get compromised?
Were there bruteforce attempts for that user?
Did the user log in from another internal host to the system we are investigating?
If so, then that means the attacker performed lateral movement as well This means more compromised hosts exist in our network, which will expand the scope of the incident.
If the user login was not from some internal host but was through RDP from the internet, were there brute force attempts? Consider the following:
🔎 Is there a login from a country where our organization doesn't have employees there?
🔎 Was the time of login outside business hours?
🔎 Then that strongly suggests a credentials leak.
Attackers buy remote access credentials through initial access brokers on the dark web. If that is the source of it, then our security posture might need an attack surface reduction.
This all was formulated from a single event. Analysts need to be open and sharp-minded and ask the right questions if they truly want to master the art of defense.
Master Windows event log analysis with HTB Academy

-
Gain practical skills for investigating Windows event logs to uncover potential security breaches.
-
Learn the process of installing or updating Sysmon and present real-world examples of detection, including identifying DLL hijacking, unmanaged PowerShell/C-Sharp injection, and credential dumping.
-
Delve into Event Tracing for Windows (ETW) and its architecture, learn its components, and how to interact with it.
Components of event logs
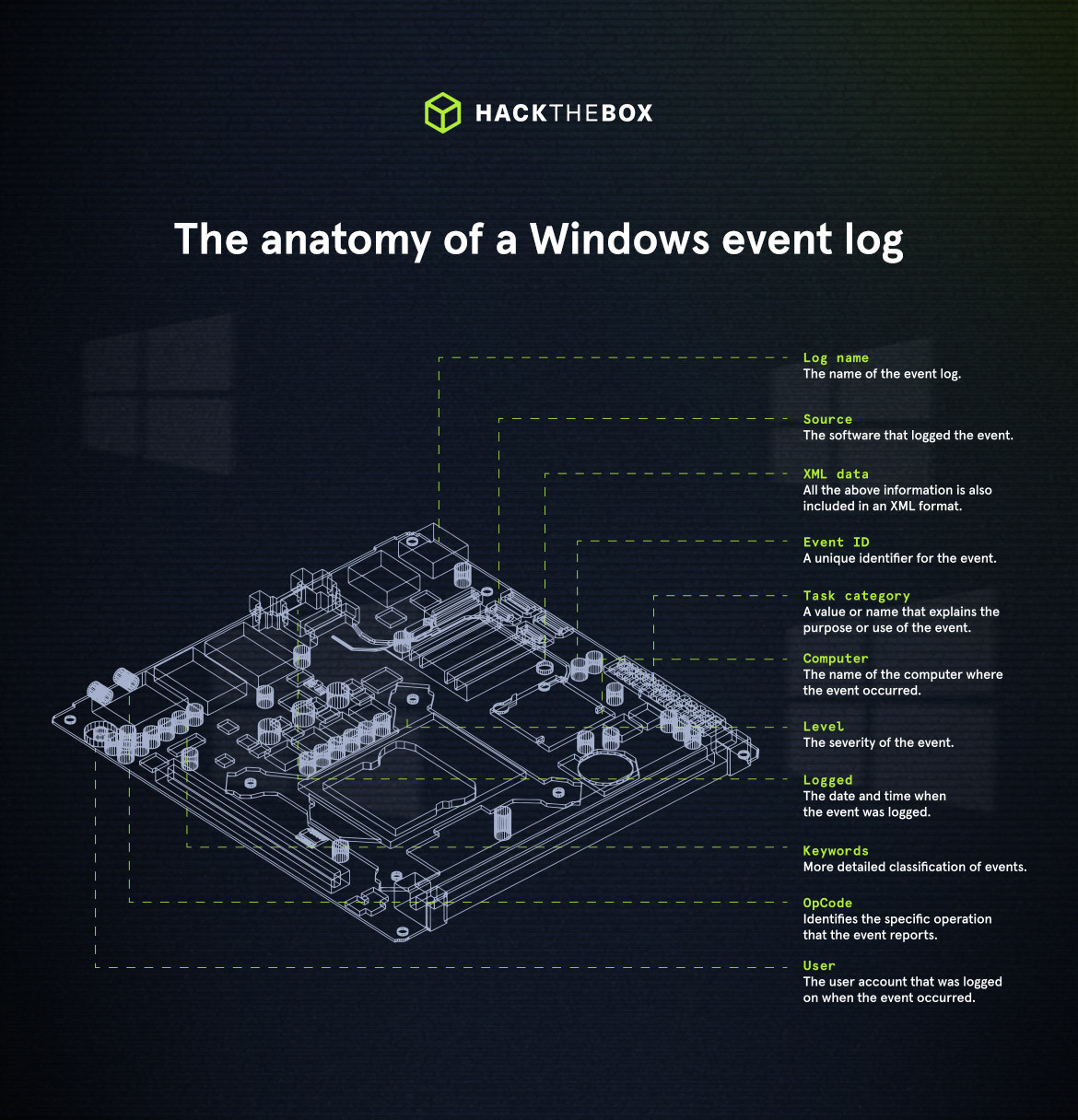
When examining Application logs, we encounter two levels of events: information and error.
Information events provide general usage details about the application, such as its start or stop events. While error events highlight specific errors and offer detailed insights into the encountered issues.
Each entry in the Windows event log contains the following components:
-
Log name: the name of the event log (e.g., Application, System, Security, etc.).
-
Source: the software that logged the event.
-
Event ID: a unique identifier for the event.
-
Task category: this often contains a value or name that can help us understand the purpose or use of the event.
-
Level: the severity of the event (Information, Warning, Error, Critical, and Verbose).
-
Keywords: flags that allow us to categorize events in ways beyond the other classification options. These are generally broad categories, such as "Audit Success" or "Audit Failure" in the Security log.
-
User: the user account that was logged on when the event occurred.
-
OpCode: this field can identify the specific operation that the event reports.
-
Logged: the date and time when the event was logged.
-
Computer: the name of the computer where the event occurred.
-
XML data: all the above information is also included in an XML format along with additional event data.
💡The keywords field is particularly useful when filtering event logs for specific types of events. It can enhance the precision of search queries by allowing us to specify events of interest, making log management more efficient.
Essential Windows event logs
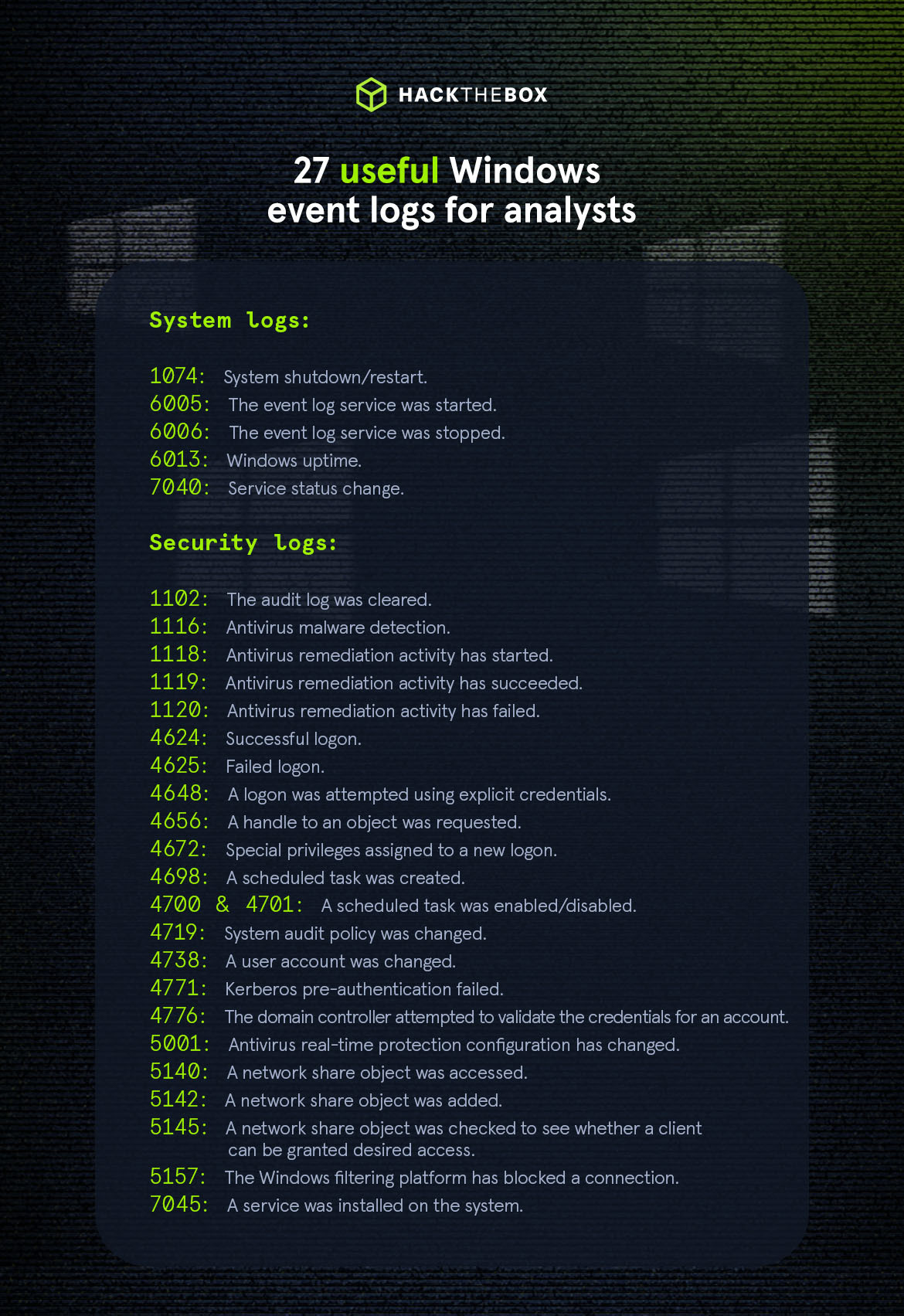
You'll encounter plenty of different Windows event logs when performing an analysis.
Here are some of the most useful ones to be aware of:
Windows system logs:
|
Event ID |
Description |
|
1074 System shutdown/restart. |
By monitoring these events, you can determine if there are unexpected shutdowns or restarts, potentially revealing malicious activity such as malware infection or unauthorized user access. |
|
6005 The event log service was started. |
This is an important record, as it can signify a system boot-up, providing a starting point for investigating system performance or potential security incidents around that period. It can also be used to detect unauthorized system reboots. |
|
6006 The event log service was stopped. |
This is typically seen when the system is shutting down. Abnormal or unexpected occurrences of this event could point to intentional service disruption for covering illicit activities. |
|
6013 Windows uptime. |
This event occurs once a day and shows the uptime of the system in seconds. A shorter-than-expected uptime could mean the system has been rebooted, which could signify a potential intrusion or unauthorized activity on the system. |
|
7040 Service status change. |
This event indicates a change in service startup type, which could be from manual to automatic or vice versa. If a crucial service's startup type is changed, it could be a sign of system tampering. |
Windows security logs:
|
Event ID |
Description |
|
1102 The audit log was cleared. |
Clearing the audit log is often a sign of an attempt to remove evidence of an intrusion or malicious activity. |
|
1116 Antivirus malware detection. |
Logs when Windows Defender detects malware. A surge in these events could indicate a targeted attack or widespread malware infection. |
|
1118 Antivirus remediation activity has started. |
Signifies that Defender has begun the process of removing or quarantining detected malware. It's important to monitor these events to ensure that remediation activities are successful. |
|
4624 & 4625 Successful and unsuccessful logon |
This information is vital for establishing normal user behavior. Abnormal behavior, such as login attempts at odd hours or from different locations, could signify a potential security threat. |
|
4672 Special privileges assigned to a new logon. |
This event is logged whenever an account logs on with super user privileges. Tracking these events helps to ensure that super user privileges are not being abused or used maliciously. |
|
4700 & 4701 A scheduled task was enabled/disabled. |
Scheduled tasks are often manipulated by attackers for persistence or to run malicious code, so these logs can provide valuable insight into suspicious activities. |
|
4719 System audit policy was changed. |
It could be a sign that someone is trying to cover their tracks by turning off auditing or changing what events get audited. |
💡The key to spotting anomalies is understanding what’s considered “normal” in our environment. For example, regular changes in system audit policies (4719) could be normal in your organization but considered a threat in another. Learning your environment is an essential first step.
Practice Windows event log analysis on HTB Sherlocks
Put your skills to the test with our defensive Machines in Sherlocks. The following focus on Windows event log analysis:
| LogJammer | Tracer | Hunter |
|
You have been presented with the opportunity to work as a junior DFIR consultant for a big consultancy, however, they have provided a technical assessment for you to complete. The consultancy Forela-Security would like to gauge your knowledge on Windows event log analysis. Please analyze and report back on the questions they have asked. |
A junior SOC analyst on duty has reported multiple alerts indicating the presence of PsExec on a workstation. They verified the alerts and escalated the alerts to tier II. As an incident responder, you triaged the endpoint for artifacts of interest. Now please answer the questions regarding this security event so you can report it to your incident manager. |
A SOC analyst was alerted about possible lateral movement and credential-stuffing attacks. As part of the incident response team, you are assigned the incident ticket. You are provided with the Artifacts acquired from the endpoint and the limited network capture for analysis. Now you must conduct a deep dive with the provided data sources to understand how the incident occurred. |
|
Tools you’ll use:
|
Tools you’ll use:
|
Tools you’ll use:
|
How to analyze suspicious activity with Windows event logs and Sysmon
So, now that we know what logs to look for, how can we go about identifying suspicious activity?
This is where Windows System Monitor (Sysmon) can be used to our benefit.
Sysmon is a Windows system service and device driver that monitors and logs system activity to the Windows event log. Sysmon provides detailed information about process creation, network connections, changes to file creation time, and more.
Sysmon's primary features include:
-
A Windows service for monitoring system activity.
-
A device driver that assists in capturing the system activity data.
-
An event log to display captured activity data.
Sysmon's unique capability lies in its ability to log information that typically doesn't appear in the security event logs.This makes it a powerful tool for deep system monitoring and cybersecurity forensic analysis.
To get started, you can install Sysmon by downloading it from the official Microsoft website. Once downloaded, open an administrator command prompt and execute the following command to install Sysmon.
C:\Tools\Sysmon> sysmon.exe -i -accepteula -h md5,sha256,imphashTo utilize a custom Sysmon configuration, execute the following after installing Sysmon.
C:\Tools\Sysmon> sysmon.exe -c filename.xmlLog collection using Sysmon
Sysmon logs are stored in the Windows event logs in an XML format. To access the Sysmon, navigate to event viewer → Applications and Services Logs → Microsoft → Windows → Sysmon. A detailed summary of every event gets listed with its associated event IDs.
Want to collect logs more efficiently? Well, have you heard of a SIEM?
Take a look at our Academy module on Security Monitoring & SIEM Fundamentals to learn more.
Event log storage and retention
An important step is to establish a log storage and retention strategy to ensure you can store logs and retain them for the required period.
Depending on your organization's needs and compliance requirements, you may choose to store logs locally on each system or centrally in a log management system.
Windows event log analysis with Sysmon
When it comes to analyzing Sysmon logs in particular, it’s important to note that there is a different set of event IDs to be aware of, here are some of the most important:
|
Sysmon event ID |
Description |
|
1 ProcessCreate |
Detailed information about the process created, including name, command line options, parent processes, and user accounts. |
|
3 NetworkConnect |
Records network connections including information on source and destination IP addresses, port numbers, and the process responsible for making each connection. |
|
6 DriverLoad |
Can help identify potentially malicious drivers that threaten system security. |
|
11 FileCreate |
File creation events play a critical role in detecting malicious files or temporary files used during an attack. |
|
12, 13 & 14 Registry events |
Relate to registry events that provide information on any changes made to Windows registry files, such as adding or changing accounts or system settings. |
The full list of Sysmon event IDs can be found here.
For threat hunters and incident responders, Sysmon can be used to create queries to look for indicators of unusual activity or recognized attack patterns. With this method, you can spot security flaws or possible risks that aren't always obvious.
Logs can also be used to reconstruct timelines, track attacker actions, and determine the impact of security incidents.
For more examples of using Sysmon to identify threats, please explore our Academy module on: Windows Event Logs & Finding Evil.
Strengthen defenses and stop attackers in their tracks
Mastering event log analysis is essential for threat hunters, SOC analysts, incident responders, and anyone in the cybersecurity industry. Not only is it required from a regulatory standpoint, but also can help stop attackers before they get into your system.
Understanding these logs can help us form a narrative and understand why a system was compromised. These learnings can prevent similar incidents from reoccurring.
Essential Hack The Box resources for event log analysis:
Whether you're an aspiring analyst or SOC lead growing your blue team, HTB Certified Defensive Security Analyst (HTB CDSA) gets security analysts job-ready.
|
Author Bio: Sabastian Hague (sebh24), Defensive Content Lead, Hack The Box Sabastian Hague is a seasoned cybersecurity professional with over eight years of experience in the field. After serving in the Royal Air Force as a specialist in all things SOC, he went on to work for Vodafone's global CERT team before taking on a role as a senior security consultant with SpiderLabs and working on numerous high-profile incidents. He is now the Defensive Content Lead at Hack The Box. Seb has numerous industry certifications, including GIAC Certified Detection Analyst (GCDA), GIAC Continuous Monitoring Certification (GMON), GIAC Certified Incident Handler (GCIH), GIAC Certified Intrusion Analyst, Offensive Security Certified Professional (OSCP), Blue Team Level 1 (BTL1), Blue Team Level 2 (BTL2), Cybereason Threat Hunter (CCTH). |






