Cyber Teams
9 critical cybersecurity trends for 2024
What security trends are actually worth your time? Senior cybersecurity professionals from the community and HTB’s experts weigh in on nine cybersecurity trends for 2024.

sebh24,
Jan 19
2024
Table of Contents
- Cybersecurity trends for 2024
- 1. Generative AI for analysts
- 2. Addressing cybersecurity burnout (a surprising solution)
- 3. Cloud security will be a key priority
- 4. Upskilling and reskilling will be more important than ever
- 5. More value placed on Identity and Access Management (IAM)
- 6. Blurring the lines between red and blue
- 7. Changing cybersecurity success metrics
- 8. More investment in proactive cybersecurity tactics
- 9. Continued disruption from ransomware
- Proactively strengthen your defenses for 2024
As we enter the new year, we step into an environment teeming with emerging threats, evolving tech, and broader attack surfaces. This brings new opportunities and challenges (along with some inflated trends) for security pros to be aware of.
Amidst the sea of trends and priorities, which ones truly matter for your team in 2024?
With the rapid development of AI introducing new vulnerabilities and the alarming rise in ransomware attacks, cybersecurity professionals need to evaluate plenty of risks and trends.
But it’s not all about threats. There’s a notable shift in how leaders and teams view “the world of work” in cybersecurity. Among the thousands of security teams who train with HTB, we’ve observed a growing trend of leaders placing greater emphasis on the well-being and retention of their staff.
In fact, in our Cyber Attack Readiness Report, which surveyed 803 active cybersecurity professionals, we found that over 60% see upskilling as a solution to burnout.
So it’s clear that cybersecurity leaders are considering upskilling programs and retention strategies to bolster team performance and security posture.
All of this and more are covered in our top cybersecurity trends for 2024.
Cybersecurity trends for 2024
1. Generative AI for analysts
The release of generative AI dominated the industry in 2023, so it’s no surprise that we can expect a significant impact on cybersecurity in 2024. While many organizations are considering AI from an offensive security perspective, there’s plenty to explore for analysts.
We spoke to Sabastian Hague (sebh24), our Defensive Content Lead at Hack The Box, on the role of generative AI for analysts in 2024:
Why is generative AI important for analysts, and what’s its role?
“Let's make one thing clear–understanding the intricacies of AI is really complex, requiring specialized knowledge akin to a PhD level. Recent technologies have, however, completely transformed this space.
The advent of user-friendly platforms has made these powerful tools accessible to a much broader audience, for example, analysts.”
Analysts no longer need to be experts to leverage the capabilities of AI, meaning it can assist in the response and analysis of security incidents.
Sabastian Hague (sebh24), Defensive Content Lead at Hack The Box.
How does generative AI impact cybersecurity?
Generative AI is slowly becoming an indispensable ally to blue teams across the globe. If used correctly, generative AI may have a net positive impact allowing defenders to streamline processes, save time, and further fortify our defenses.
Sabastian Hague (sebh24), Defensive Content Lead at Hack The Box.
“However, it's crucial to remember that AI is a tool to augment, not replace, the expertise of seasoned cybersecurity professionals. The nuanced judgment and experience of these professionals are irreplaceable, especially in interpreting complex threat landscapes and making critical security decisions.”
What are generative AI use cases in 2024?
“The use cases of generative AI have expanded rapidly in 2023, meaning this will likely only increase in 2024. Some of the use cases I can see occurring in 2024 within the context of analysts and DFIR are detailed below:
-
Enhanced Incident Response Automation.
-
Assistance in automating routine SOC tasks.
-
Automated Reporting and Documentation.
-
Large Data Analysis Assistance.”
Learn to defend and exploit AI threats with Dedicated Labs
Our Dedicated Labs track provides insights into common attacks on Artificial intelligence (AI) and Machine Learning (ML) systems, emphasizing underlying principles and demonstrating how insecure implementations may compromise sensitive information or enable unauthorized access.
-
Identify and exploit insecure ML implementations.
-
Exploit classic vulnerabilities through AI systems.
-
Bypass Face Verification Systems.
-
Basic Prompt Injection techniques.
-
Write Machine Learning programs in Python.
-
Privacy attacks on Machine Learning models (white-box and black-box).
-
Train classification models for Membership Inference attacks.
2. Addressing cybersecurity burnout (a surprising solution)
The significant cybersecurity talent shortage leads to more issues than a lack of skills. It places additional pressure on existing cybersecurity teams who are stretched thin in an already demanding environment.
This is set to continue in 2024, but we expect to see a general culture shift towards addressing burnout and supporting the wellbeing of cybersecurity teams.
Yet increasing pay or offering more vacation time isn’t always the solution. Instead, providing opportunities for cybersecurity professionals to develop and learn new skills is a highly effective way to keep them engaged.
This was proven in our Cyber Attack Readiness report after speaking to 803 active cybersecurity professionals. More than 70% of managers view team events like Capture The Flag (CTFs) as a viable way to boost employee engagement. Showing there are plenty of ways we can address burnout in 2024 (without raising salaries).
Recommended read: A cybersecurity reskilling guide for leaders.
3. Cloud security will be a key priority
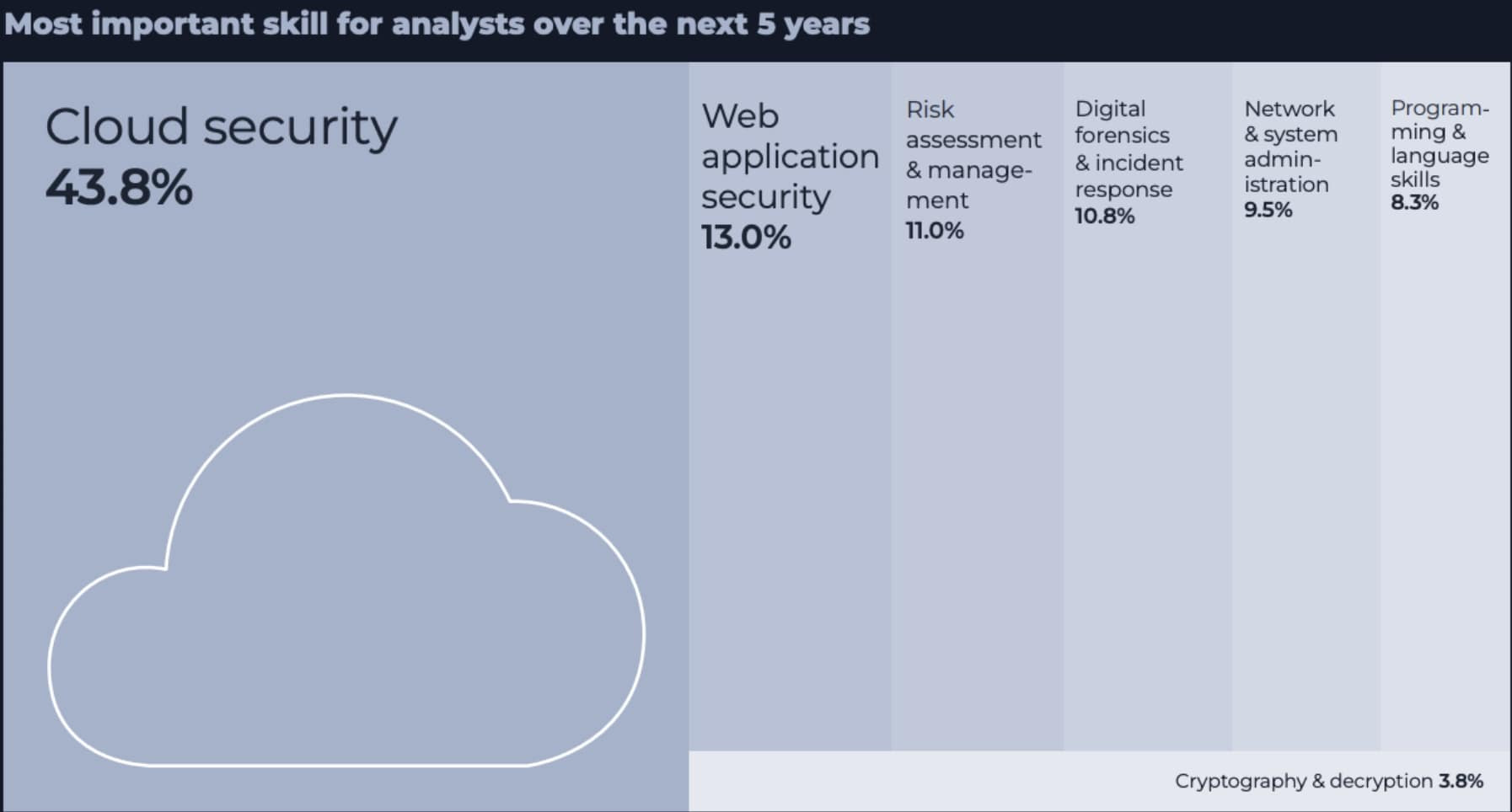
After surveying 400 active cybersecurity professionals in the HTB database, we found that over 40% believe cloud security skills will be a key priority for SOC analysts over the next five years.
We spoke to Dave Elliott (Blitztide), Senior Content Engineer at Hack The Box, about the trending risks to cloud security in 2024 and what organizations can do about it:
The largest security risks in the cloud environment are misconfigured Identity and Access Management (IAM), poor key lifecycle management, and poor cloud asset management.
Dave Elliott (Blitztide), Senior Content Engineer at Hack The Box
“Misconfigured IAM can lead to greater exposure to phishing/vishing attacks, as without proper Multi-Factor Authentication (MFA) for services, a keen attacker can get instant access to an account with high privileges and lock the original user out.
Further issues with poor IAM would be the increased risk of insider threat. Handing out keys and credentials that have overreaching permissions may be simple in the short term, however, it allows disgruntled employees to tear down your organization’s cloud real-estate.
This leads to key management, each access key should be short-lived (up to your risk profile) and be regularly audited and regenerated to ensure attackers cannot use keys that get exposed at a later date.
Proper asset management in the cloud can be hard, but you cannot fix what you cannot see. Tools such as Amazon CloudWatch show you which services are still in use, or if they are using more resources.”
Dave recommends bolstering your cloud defenses by doing the following in 2024:
-
IAM: granular permissions should be granted only to necessary users, credentials managed promptly, and the removal of credentials ensured upon termination of employment.
-
Asset identification: requires regular reconciliation of cloud assets for accuracy. Granularity in logs is essential for extracting key security and business information, but it should be measured to avoid unnecessary costs and fatigue for analysts.
-
Costs associated with cloud security must be considered, while applying all available controls and having a vigilant Security Operations Center (SOC) team can enhance security, compromises may be necessitated by the reality of costs.
-
Decision-making on enabling or disabling specific cloud services should be guided by a robust risk management process to strike an optimal balance between security and financial considerations.
Put your team’s cloud defensive skills to the test with our Sherlocks Labs:
| Nubilum 1 | Nubilum 2 |

Scenario: Our cloud administration team recently received a warning from Amazon that an EC2 instance deployed in our cloud environment is being utilized for malicious purposes. |

Scenario: A user reported an urgent issue to the helpdesk: an inability to access files within a designated S3 directory. This disruption has not only impeded critical operations but has also raised immediate security concerns. The urgency of this situation demands a security-focused approach. |
4. Upskilling and reskilling will be more important than ever
Upskilling is no longer a “nice to have”. It’s necessary to build effective cybersecurity teams that remain loyal to your organization.
Due to the ever-widening skills gap, cyber talent is highly sought-after, meaning leaders need to offer more than just a salary to keep employees engaged.
In our Cyber Attack Readiness report, we interviewed 803 cybersecurity professionals. We found that 68% of security team members rated “opportunities to learn skills” as the most successful way of staying engaged at work.
Reskilling is a significant trend we expect to see in 2024. Companies will use existing talent to fill gaps within their cybersecurity team and improve their security posture. For example, companies may reskill their developers to vet third-party code to avoid supply chain attacks.
Reskill into cybersecurity

Why choose HTB Senior Web Penetration Tester job role path?
-
Reskilling opportunities: featuring black box AND white box techniques, companies can reskill developers and IT roles to cybersecurity by adopting a risk mitigation mindset.
-
Highly hands-on: teams conduct advanced web penetration tests, encompassing both white box and black box approaches on multiple real-world applications.
-
Stand out with unique skills: HTB is recognized for content that builds creativity, in-depth knowledge, and outside-of-the-box thinking required for real-world incidents.
I think oftentimes we get caught up in "cyber" being a completely separate industry from anything else. But there is cyber everywhere! In finances, healthcare, even education.
Use your strengths from whatever experience you have, and simply level them up. Don't think about cyber as a brand new domain.
IT could be networking experience, so think network security! Software development is self explanatory, but think DevSecOps. Then begin bridging those gaps once you've found stability in the skills you're already bringing to the table.
Bailey Marshall, Senior Security Consultant at Mandiant.
5. More value placed on Identity and Access Management (IAM)
Identity and Access Management (IAM) is essential to manage and control digital identities.
In 2024, we expect the value of IAM to expand beyond simply granting or revoking access. Instead, the emphasis will be placed on data security, regulatory compliance, insider threats, and operational efficiency.
An IAM trend that’s growing in popularity is the zero-trust security model. This believes that no user or device, no matter their location, can be trusted.
As a result, strict authentication and authorization are required. As hybrid work continues to become the norm, this is more important than ever.
A layered approach to IAM is another trend we expect to see in 2024. Relying solely on passwords as a security measure is insufficient with today’s complex cyber threats. Instead, multi-factor authentication (MFA) and single sign-on (SSO) will become the norm, staying ahead of emerging threats and safeguarding sensitive information.
💡 Upskill your team with the most common ways to attack and defend Active Directory (AD), including IAM, in our Academy module!
6. Blurring the lines between red and blue
In our SOC Analyst report, we found that hybrid blue and red teamers are on the rise, with many cybersecurity professionals wishing to pursue a career in both roles:

We spoke to Ben Rollin (mrb3n), Head of Information Security at Hack The Box, about the role of purple teaming in 2024:
How can purple teaming strengthen offensive and defensive security?
“Purple teaming facilitates knowledge sharing between the red and blue team, which reveals gaps in the organization's security program and works towards the best way to address the identified issues.
It helps members of the blue team to gain an understanding of how attackers operate in a simulated environment to be able to visualize real-world tactics, techniques, and procedures (TTPs) and be better positioned to defend against attackers.
Ben Rollin (mrb3n), Head of Information Security at Hack The Box
Offensive security teams within an organization benefit by being able to hone their skills at emulating real-world attackers while remaining stealthy with feedback from the blue team.
They’ll discover at what threshold of testing they were detected so they can adjust their own TTPs to, in turn, be able to better monitor the blue team's detection and defensive abilities on future tests.”
💡 Recommended read: Active directory hardening checklist.
What’s an example of a purple teaming exercise that organizations could simulate?
“An organization could perform an exercise where the red team begins an Active Directory related attack within the internal network to see at what threshold the attack tactics are discovered and even blocked.
Once discovered, the red team can move on to attack a different portion of the network, trying to remain as stealthy as possible until the blue team discovers them once again (or not at all).
Afterward, the purple team would facilitate knowledge sharing between the red and blue teams. This way, the red team will be able to adjust their techniques to attempt to better evade detection during future exercises.”
Our Sherlocks Labs facilitate purple team upskilling with defensive and offensive versions of Machines for the full 360 learning experience:
|
Sherlocks |
Offensive |
|
There’s been a potential security breach within Forela's internal network. It’s your job to investigate, putting your digital forensics and network security skills to the test. |
Exploit an unauthenticated arbitrary file read vulnerability, gaining full administrative access to the machine. |
|
A critical alert has been raised over a newly implemented Apache Superset setup. You need to investigate and confirm the presence of any compromise. |
Test your web application skills as you attempt to exploit a vulnerability in Apache Superset. |
|
You have been tasked with the analysis of artifacts from a potentially compromised GitLab server. |
Explore how you can exploit and gain a foothold in a GitLab server. |
7. Changing cybersecurity success metrics
With CISOs becoming a part of the board of directors, working closely with CEOs and CSOs, there’s more emphasis on outcome-driven metrics and reducing risk than ever.
The C-suite speaks a different language to cybersecurity teams, meaning key KPIs must be aligned closely with business goals.
According to research by Gartner, the following outcome-driven metrics are predicted for 2024:
-
Reduce employee-driven cybersecurity incidents by 40%.
-
45% of CISOs will expand their responsibilities beyond cybersecurity.
-
Leaders will reduce burnout-related turnover by 50%.
CISOs will be responsible for spreading cybersecurity awareness throughout organizations, and fostering a culture of understanding and vigilance regarding cybersecurity threats, best practices, and the importance of safeguarding sensitive information.
While the board needs to gain a greater understanding of cybersecurity in 2024, CISOs also need to adjust their reporting metrics and focus on outcomes directly related to company goals and workforce development.
8. More investment in proactive cybersecurity tactics
As the threat landscape evolves, many leaders adopt a proactive rather than reactive approach to cybersecurity. This involves reducing any risk at the design stage. The trend sees the technology industry willing to bake security into the earliest stages of building new applications.
This is highlighted by an increase in third-party cybersecurity risk management, as cyber teams take advantage of proactive security technologies. However, third-party technology comes with its own challenges, as threat actors target vendors and inject malicious code into applications.
Cybersecurity teams can reduce this risk by rigorously scrutinizing third-party code beforehand.
Some trending proactive security technologies and tactics for 2024 include:
-
Risk-based vulnerability management.
-
Attack surface management.
-
Security posture tools for the cloud, data, and applications.
💡Boost your defensive capabilities with our SOC Analyst job role path.
9. Continued disruption from ransomware
Ransomware attacks rose in 2023, impacting over 72% of businesses worldwide. This trend is set to continue in 2024, with plenty of solid incentives for threat actors to continue ransomware attacks due to their profitability.
Despite many countries pledging to pay the ransom no longer and instead divert the funds to rebuilding systems, this won’t stop cybercriminals from targeting high-profile enterprises for higher impact.
For many businesses, paying the ransom is the easier option to avoid disruption and reputational damage. However, this isn’t the right way to defend against ransomware. With the increase in attacks, it’s better to prepare to fight proactively:
-
Ensure your organization has offline backups.
-
Prioritize incident response plans.
-
Invest in employee cybersecurity awareness and encourage good cyber hygiene.
Prepare and respond to ransomware attacks with Sherlocks

-
Our Sherlocks Dedicated Labs teach teams to respond and analyze ransomware attacks.
-
Defend against ransomware in the cloud with Nubilum-2.
-
Learn how to reverse ransomware with our malware analysis Sherlocks.
-
Our Machines feature the latest CVEs, enabling your team to find a ransomware attack before it happens.
Proactively strengthen your defenses for 2024
To proactively improve security posture and implement successful cybersecurity workforce development plans, leaders need to filter through the noise and focus on what’s important in a sea of trends.
By shifting our focus from buzzwords to the real threats, both to our security and our teams, we’ll be in the best position to anticipate risks, strengthen defenses, and allocate resources and budget effectively in 2024.
Become an HTB Subject Matter Expert

Are you a cybersecurity professional who wants to contribute to articles like this one?
Join the HTB SME program and you’ll benefit from the following:
-
A huge audience: Our HTB community has over 2.7 million members, giving you a huge platform to share your knowledge with and feature in our editorial content.
-
Networking opportunities: Meet other HTB SMEs and expand your professional network, meeting people you may never have connected with if it wasn’t for your involvement with HTB.
-
Recognition: Any insights you provide will be credited to you, including your name, title, and LinkedIn profile. Some content will get additional love on social media too!
-
Share your experiences: We’re giving a voice to cybersecurity professionals, providing you with a platform to share your knowledge and experiences.
-
Help others: Your unique insights are incredibly valuable to other cybersecurity professionals, or even individuals just starting their careers.
💡Find out more on our blog: Become an HTB Subject Matter Expert
|
Author Bio: Sabastian Hague (sebh24), Defensive Content Lead, Hack The Box Sabastian Hague is a seasoned cybersecurity professional with over eight years of experience in the field. After serving in the Royal Air Force as a specialist in all things SOC, he went on to work for Vodafone's global CERT team before taking on a role as a senior security consultant with SpiderLabs and working on numerous high-profile incidents. He is now the Defensive Content Lead at Hack The Box. Seb has numerous industry certifications, including GIAC Certified Detection Analyst (GCDA), GIAC Continuous Monitoring Certification (GMON), GIAC Certified Incident Handler (GCIH), GIAC Certified Intrusion Analyst, Offensive Security Certified Professional (OSCP), Blue Team Level 1 (BTL1), Blue Team Level 2 (BTL2), Cybereason Threat Hunter (CCTH). |






